Cybersecurity researchers are warning about an ongoing wave of attacks linked to Raspberry Robin, a Windows malware with worm-like capabilities.
Describing it as a “persistent” and “spreading” threat, Cybereason said it observed several victims in Europe.
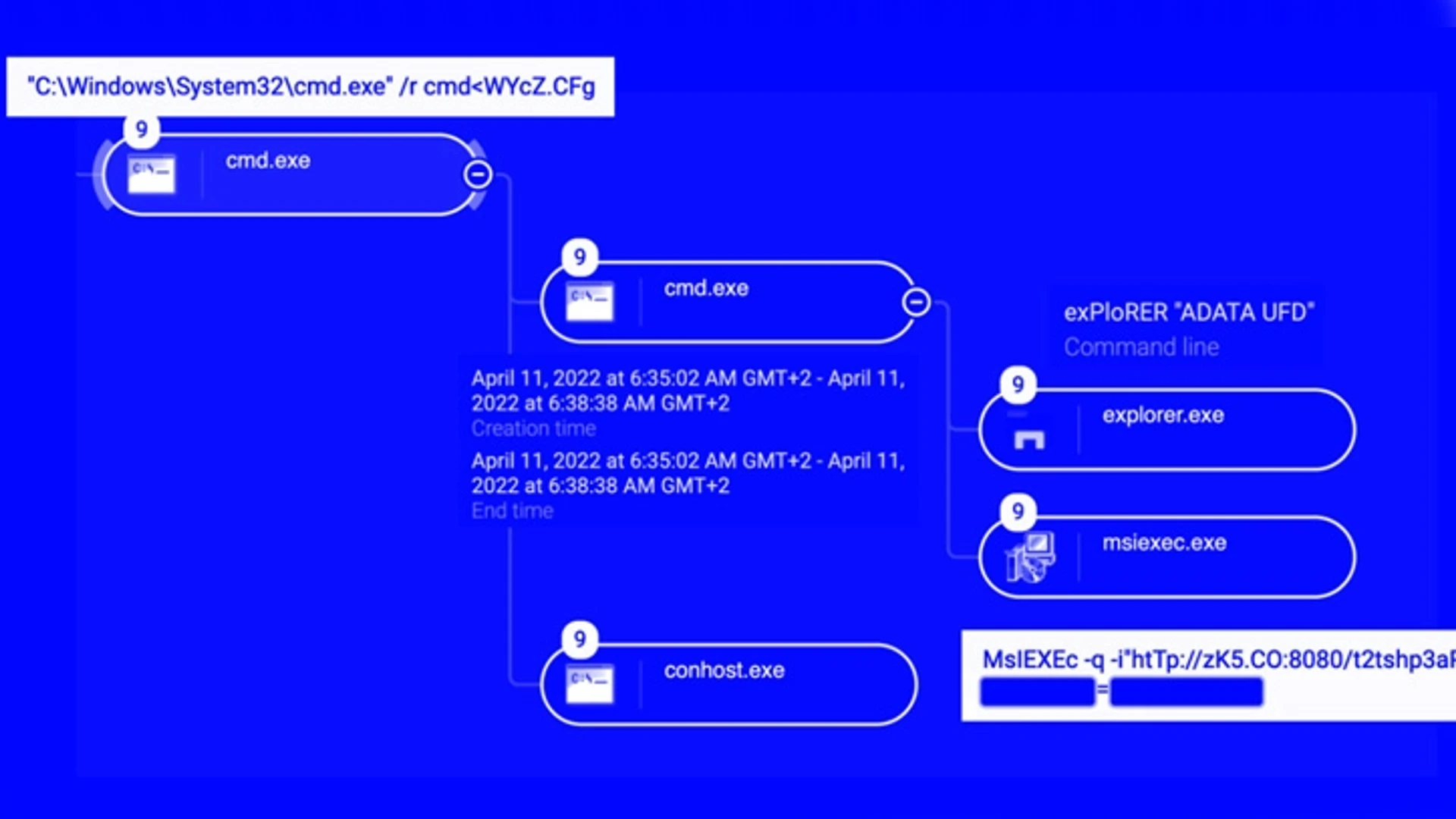
Infections are spread by worms that utilise compromised QNAP network-attached storage (NAS) devices for command and control and spread over removable USB devices containing malicious .LNK files. Researchers from Red Canary first documented it in May 2022.
Also codenamed QNAP worm by Sekoia, the malware leverages a legitimate Windows installer binary called “msiexec.exe” to download and execute a malicious shared library (DLL) from a compromised QNAP NAS appliance.
“To make it harder to detect, Raspberry Robin leverages process injections in three legitimate Windows system processes,” Cybereason researcher Loïc Castel said in a technical write-up, adding it “communicates with the rest of [the] infrastructure through TOR exit nodes.”
Persistence on the compromised machine is achieved by making Windows Registry modifications to load the malicious payload through the Windows binary “rundll32.exe” at the startup phase.
The campaign, which is believed to date back to September 2021, has remained something of a mystery so far, with no clues as to the threat actor’s origin or its end goals.
In a statement, QNAP said it is actively investigating a new wave of Checkmate ransomware infections targeting its devices, following attacks such as AgeLocker, eCh0raix, and DeadBolt.
“Preliminary investigation indicates that Checkmate attacks via SMB services exposed to the internet, and employs a dictionary attack to break accounts with weak passwords,” the company noted in an advisory.
“Once the attacker successfully logs in to a device, they encrypt data in shared folders and leave a ransom note with the file name “!CHECKMATE_DECRYPTION_README” in each folder.”
Taiwanese company QNAP recommends customers don’t expose SMB services to the internet, improve password strength, take regular backups, and update the operating system to the latest version as precautionary measures.